Google reveals a massive malware campaign infecting over 10 million Android devices. The malware primarily targets low-cost TV streaming boxes, tablets, and projectors, primarily from China. TF investigates the details, explains why this matters, and what users and manufacturers should be aware of.
What’s Happening & Why This Matters
Google files a lawsuit in New York against a criminal operation spreading a malware called BadBox 2.0. This botnet infects millions of devices, creating a network of compromised hardware that cybercriminals can exploit. The malware primarily affects Android devices, particularly those running open-source versions that lack Google’s security features.
BadBox 2.0 primarily spreads through inexpensive, unbranded devices sold worldwide; some come pre-installed with the malware. Others get infected when users install Trojanized apps from unofficial app stores. Hackers can rent access to these infected devices, using them for cybercrimes like ransomware or distributed denial-of-service (DDoS) attacks. This vast botnet could become a launching pad for large-scale hacking operations that impact U.S. and global networks.

Google’s lawsuit identifies specific Android TV box models targeted by BadBox 2.0, including X88 Pro 10, T95, MXQ Pro, and QPLOVE Q9. Google accuses at least 25 individuals or entities, mostly based in China, of orchestrating this operation. The company requests that the court shut down domains linked to the botnet, which are hosted by services like Cloudflare, GoDaddy, and NameCheap.
In addition to cyberattacks, the malware generates fraudulent clicks on mobile ads, creating an additional stream of illegal profits for its operators. Google warns users to disconnect affected devices to prevent further exploitation.
What is BadBox 2.0?
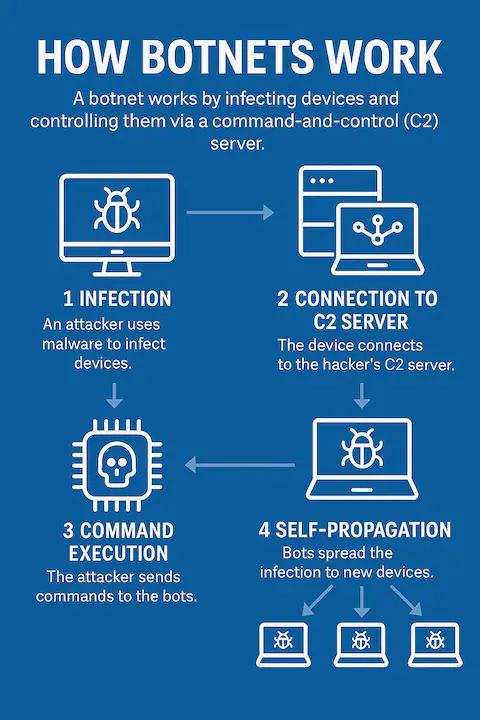
BadBox 2.0 is the largest known botnet targeting internet-connected Android TV devices. Google warns that this malware’s infrastructure allows it to adapt to various criminal activities; adaptability makes it a particularly flexible, dangerous threat. This botnet’s growth means it can scale quickly, escalating the risk to global cybersecurity.
The malware’s prevalence in devices with limited security protection exposes a gap in the Android ecosystem, especially for open-source builds. The malware establishes a need for stronger security protocols and stricter control over the supply chain of low-cost electronics. Cheapily made devices often serve as entry points for cybercriminals.
Security Insights
Google states, “This lawsuit enables us to dismantle the criminal operation behind the botnet, cutting off their ability to commit more crime and fraud.” Its legal action is a rare step where a company is directly targeting the cybercrime networks’ infrastructure.
Security researchers and the FBI have already flagged the threat. The lawsuit is Google’s first salvo seeking a permanent injunction to stop the botnet’s operation. Success equals protection for millions of users globally.
If you own one of the identified devices, unplugging it is the safest course of action. Since the malware can operate in the background, continuously generating fraudulent activity and participating in attacks, users must exercise caution. Checking device provenance and installing software only from trusted sources helps prevent such infections.
TF Summary: What’s Next
Google’s lawsuit against BadBox 2.0 operators marks a crucial effort to disrupt a vast cybercrime network. By targeting the botnet’s command-and-control servers, Google aims to dismantle its infrastructure and stop further attacks and fraud.
The Badbox situation identifies risks posed by low-cost, poorly secured Android devices worldwide. Users, manufacturers, and regulators must collaborate to improve security standards and prevent future malware outbreaks. Maintaining devices updated, sourcing trusted vendors, and proactive vigilance reduce risks.


