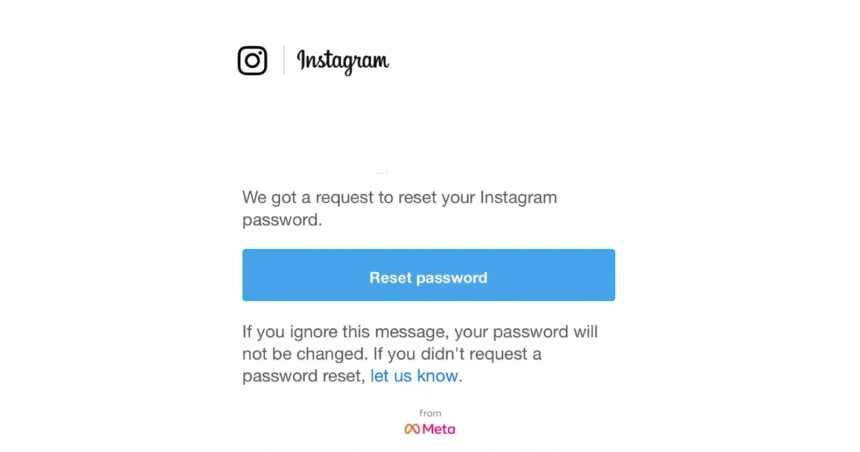
Password Reset Emails Trigger Confusion
Over the weekend, millions of Instagram users opened their inboxes to an unsettling surprise. Legit-looking emails asked them to reset their passwords. For many, the timing felt wrong. No login attempt. No forgotten password. Just a reset request out of the blue.
Almost immediately, questions spread across social media. Users worried about hacked accounts. Security researchers raised alarms. Instagram immediately denied a breach, saying its systems stayed intact and user data stayed secure. That explanation calmed some fears. It also raised new ones.
What’s Happening & Why This Matters
The incident began when users across multiple regions received official Instagram password reset emails without requesting them. The emails contained valid links. They routed users to legitimate Instagram flows. Nothing about them looked like classic phishing.
That detail matters. Scam emails often fail basic checks. These did not.
Instagram soon acknowledged the issue. The company stated that an external party exploited a flaw that allowed them to trigger password reset emails at scale. Instagram said it fixed the issue quickly and blocked further abuse. The company noted one point repeatedly: no internal systems suffered compromise.
A spokesperson told reporters, “We fixed an issue that let an external party request password reset emails for some people. There was no breach of our systems, and accounts remain secure.”

What Security Researchers Say
Not everyone accepts that explanation at face value.
Cybersecurity firm Malwarebytes publicly challenged Instagram’s claim. The firm pointed to underground forums advertising a dataset tied to 17.5 million Instagram accounts. According to Malwarebytes, the dataset includes usernames, phone numbers, email addresses, and location details.
In a widely viewed post, the company stated that the password reset emails correlate with the circulation of this data. That post gained millions of views within hours.
Other researchers offered a more nuanced take. Some believe the data originates from older scraped datasets, assembled using publicly visible profile information rather than a fresh system intrusion. That theory suggests attackers used existing data to automate reset requests rather than break into Instagram’s core infrastructure.
Instagram declined to identify the “external party” involved or explain precisely how the abuse occurred.
Why This Episode Still Matters
Even if no breach occurred, the incident exposes a deeper issue: erosion of trust in platform security capabilities.
Password reset emails serve as a last-line warning. When those signals trigger falsely, users face a dilemma. Ignore them and risk compromise. Click them and risk training themselves into unsafe habits.
The episode also represents how API behavior and automation loopholes create real-world panic even without direct data theft. At scale, perception becomes reality.
As one independent security analyst noted, “You don’t need a breach to cause damage. Confusion alone erodes confidence.”
TF Summary: What’s Next
Instagram claims the issue is fully resolved. No further unauthorised reset requests are occurring. Users who received emails can safely ignore them or reset passwords directly through the official app. Adding two-factor authentication remains the strongest defensive step.
The broader lesson cuts deeper. Platforms need more transparent, faster communication during security scares. Vague explanations leave room for speculation, especially when third-party researchers publish conflicting claims. Transparency matters as much as technical fixes.
MY FORECAST: Expect stricter rate-limiting, clearer audit trails, and tighter reset verification across major platforms. Password reset abuse now sits squarely on the security roadmap, not the edge cases.
— Text-to-Speech (TTS) provided by gspeech