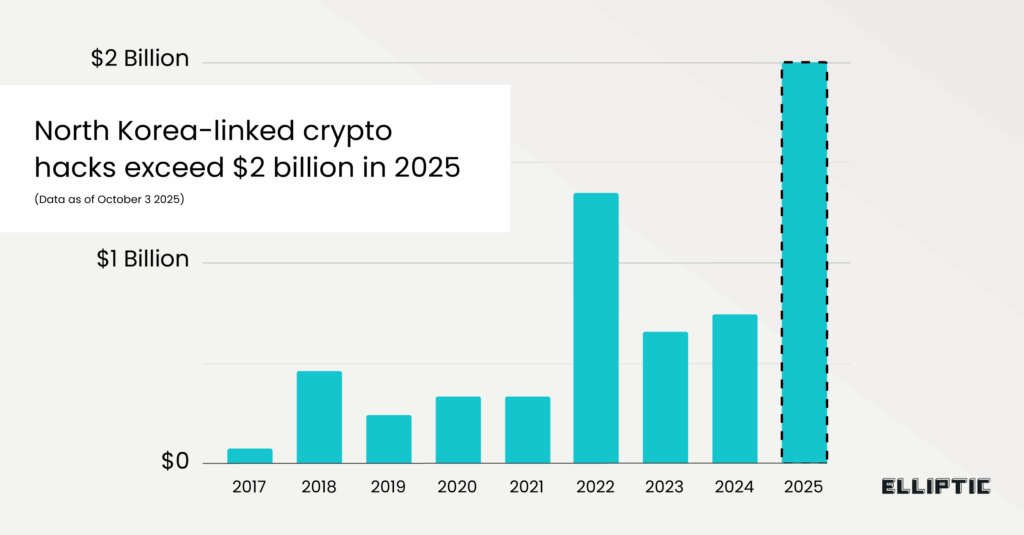
North Korean hackers are breaking records again — and not the kind worth celebrating. The North Korean crypto hacks are becoming a serious concern. According to Elliptic, a blockchain analytics firm, North Korean cybercriminals have already stolen more than $2 billion in cryptocurrency so far in 2025. This makes it the most profitable year on record for the regime’s hacking operations.
What’s Happening & Why This Matters

The hackers — believed to be state-sponsored and linked to groups like Lazarus — have targeted both major exchanges and private wallets. Their attacks form part of a long-running campaign to fund Pyongyang’s weapons programs and circumvent international sanctions. The scale and sophistication of these hacks reveal a deepening entanglement between cybercrime and global security concerns.
A Record-Breaking Heist Year
The biggest singular heist of the year happened in February, when hackers siphoned off more than $1.4 billion from the Bybit exchange. This was the largest crypto theft in history. Investigators found that the attackers first breached a digital wallet provider. This breach gave them access to an offline or “cold” wallet that held around 400,000 Ethereum coins.
Bybit later reported that about 68% of the stolen funds remained traceable. This means only a portion was successfully laundered or cashed out. Even so, the theft underscores how vulnerable even top-tier exchanges remain. They are susceptible to state-sponsored attackers with time, resources, and patience.
In total, Elliptic attributes more than 30 separate hacks to North Korean actors this year alone. These involve platforms such as LND.fi, WOO X, and Seedify. Another blockchain analysis firm, Chainalysis, has put the total losses at approximately $2.17 billion. This confirms that North Korea’s crypto theft campaign shows no signs of slowing.
State-Sponsored Crime Meets Cyber Innovation
The data paints a clear picture: cyber theft has become a key revenue stream for the North Korean government. Despite some of the harshest economic sanctions in the world, the regime continues to find ways to fund its operations — particularly its nuclear weapons and ballistic missile programs.
A United Nations report from 2019 already warned that North Korea had stolen more than $2 billion through state-directed cyberattacks to finance its military. The 2025 figures now suggest those efforts have intensified. They have evolved into a cornerstone of North Korea’s financial strategy.
Elliptic’s research notes that the total known value of cryptoassets stolen by the regime exceeds $6 billion. This is a staggering figure that represents years of coordinated cyber warfare disguised as financial theft.
The methods are also changing. Hackers have begun targeting not just institutions but high-net-worth individuals. They use social engineering and phishing schemes to steal from personal wallets. Chainalysis reports that 23.35% of all stolen crypto this year came from individual users. This is a major increase from previous years. Attackers frequently impersonate companies, send malicious links, and plant malware disguised as legitimate apps or job offers.
A Looming Global Threat
The ongoing campaign illustrates how North Korea has mastered cyber-enabled sanctions evasion. The heists give the regime access to liquid, anonymous assets that are hard to trace and easily transferable across borders. Once stolen, the cryptocurrency is laundered through decentralized platforms, privacy coins, and a complex web of brokers and mixers. This obscures its origins.
Western governments and intelligence agencies are taking note. The U.S. Treasury Department has repeatedly sanctioned individuals and groups tied to North Korea’s cyber units, including the Lazarus Group and APT38, for their involvement in multi-million-dollar thefts. However, as cryptocurrency transactions remain pseudo-anonymous, full enforcement remains a challenge.
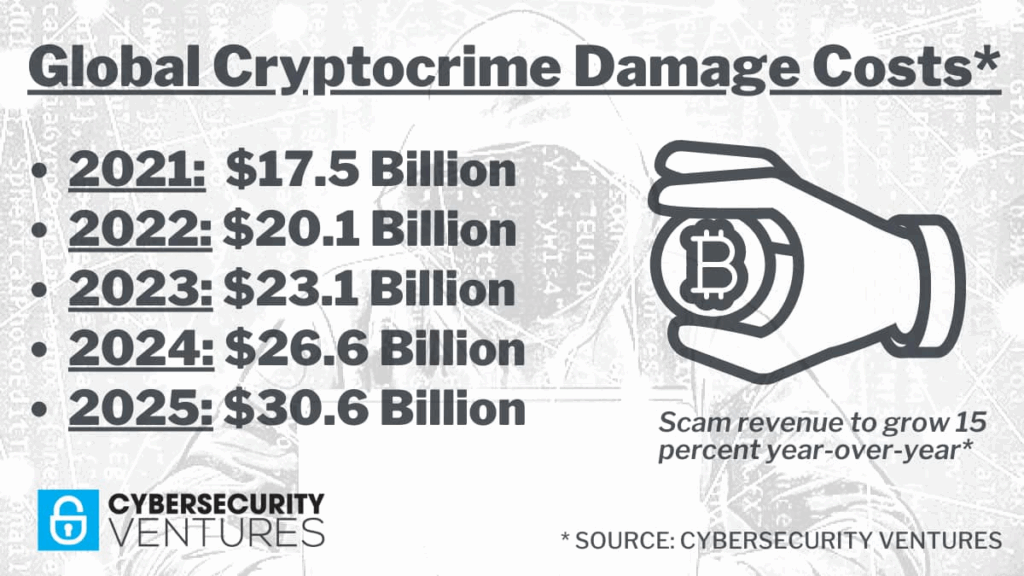
What’s more, the attacks have exposed gaps in the cyber defenses of global financial infrastructure. Even advanced exchanges that boast robust cold storage systems have proven susceptible to infiltration. Hackers often exploit human error or vulnerabilities in third-party systems to gain unauthorised access.
Experts warn that as long as cryptocurrencies remain difficult to regulate internationally, state-backed hackers, such as those in North Korea, will continue to exploit the digital loopholes left behind.
The Ripple Effect
Beyond the financial toll, these attacks erode trust in the digital asset ecosystem. Institutional investors are growing cautious about crypto exposure. They fear reputational and security risks. Exchanges are tightening security audits. Meanwhile, blockchain analytics firms such as Elliptic and Chainalysis are working with law enforcement agencies to track and freeze stolen funds before they are converted to fiat currency.
But for every recovery, multiple new attacks occur. The decentralized nature of blockchain, once heralded for democratizing finance, has become a double-edged sword. It offers both transparency and anonymity, which criminals often exploit.
As regulators and governments attempt to catch up, experts say the focus must shift from reactive measures to proactive prevention. This includes strengthening digital identity systems, mandating the sharing of real-time threat intelligence, and expanding global cooperation on cyber enforcement.
TF Summary: What’s Next
The trend of state-backed crypto theft is not slowing down. As North Korea grows more sophisticated, global regulators, blockchain developers, and financial institutions must treat cybersecurity as an existential priority, not an afterthought.
MY FORECAST: Expect more international task forces and AI-driven blockchain tracking tools to emerge in response to this escalation. Yet, until there’s a unified framework for crypto regulation, the $2 billion headline may soon look modest. North Korea’s cyber arm continues to show that for some regimes, hacking is not just espionage — it’s economic policy.
— Text-to-Speech (TTS) provided by gspeech