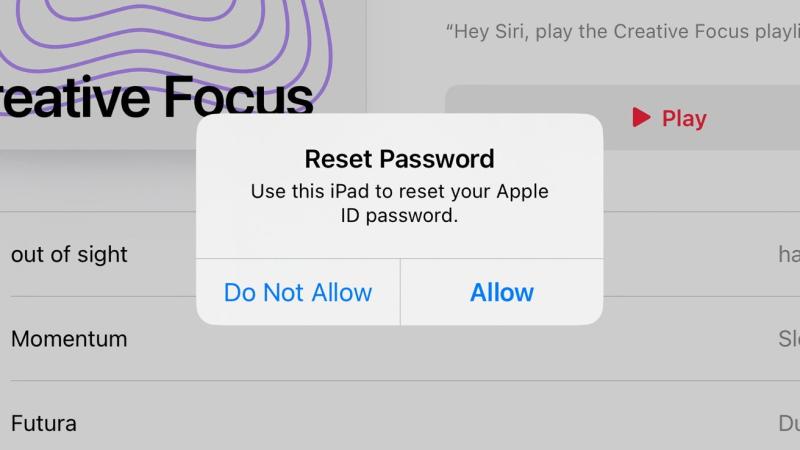
In response to a surge in phishing attacks targeting iPhone users, Apple has issued new guidelines to help protect its users’ Apple IDs and other online accounts. This article delves into Apple’s latest recommendations and the significance of these measures in safeguarding users from cyber threats.
What’s Happening & Why This Matters
Phishing attacks, especially those targeting iPhone users through SMS, have seen a noticeable increase. Cybercriminals are sending text messages that appear to be from Apple, attempting to steal personal credentials such as Apple IDs, passwords, and two-factor authentication codes.
Apple’s New Guidelines
Apple has released a support document titled “Recognize and avoid social engineering schemes including phishing messages, phony support calls, and other scams.” This guide aims to educate users on how to recognize and avoid various forms of phishing attacks.
- Do not share personal data or security information: Apple advises against sharing passwords, security codes, or other personal information with anyone.
- Enable two-factor authentication: Use Face ID or Touch ID for added security.
- Secure contact information: Always keep your contact information up-to-date and never share your Apple ID password or verification codes.
- Avoid suspicious links and attachments: Download software only from trusted sources and avoid following links or opening attachments in unsolicited messages.
- Do not use Apple Gift Cards for payments: Learn to identify legitimate Apple support emails and avoid using Apple Gift Cards for payments to others.
Jake Moore, a global cybersecurity advisor at ESET, emphasizes the importance of adhering to Apple’s advice. He stresses that users must remain aware of potential phishing threats and understand the risks involved.
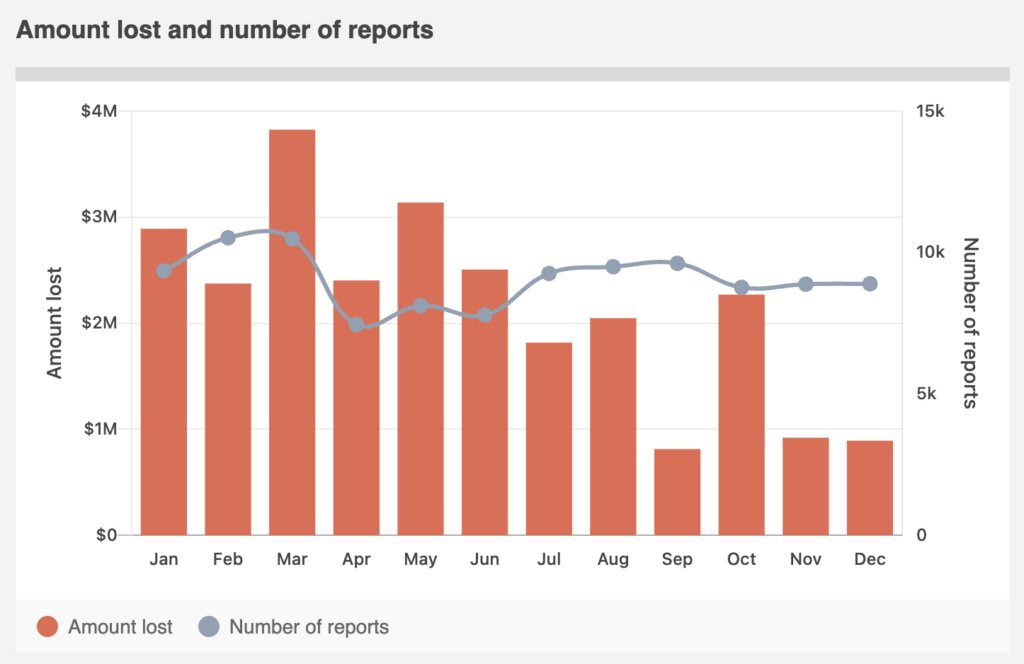
Common Phishing Tactics and Recommendations
Phishing actors often pose as trusted entities like Apple or banks, using various methods to lure victims into providing sensitive information. These include:
- SMS phishing (smishing): Text messages that appear to be from Apple, prompting users to click on fraudulent links.
- Email phishing: Emails that mimic official communication from Apple or other trusted entities.
- Phone calls: Scammers posing as Apple or bank representatives, asking for personal information.
Apple’s guidelines highlight several steps to protect against phishing:
- Be cautious with unexpected messages: Always verify the source of unexpected messages and avoid clicking on suspicious links.
- Enable multi-factor authentication: This adds an extra layer of security, ensuring only authorized users can access accounts.
- Direct contact for support: Apple support representatives will never ask for passwords, device passcodes, or two-factor authentication codes through unsolicited links or messages.
The Federal Communications Commission (FCC) advises the following additional measures:
- Keep security software updated: Ensure that security software on computers and mobile devices is always up-to-date.
- Avoid engaging with suspicious texts: Do not click links, reply to texts, or call unknown numbers from suspicious messages.
- Delete suspicious texts: Remove any texts that seem dubious or unsolicited.
- Verify contact information: If a message claims to be from a company or government agency, verify their contact details through official channels.
TF Summary: What’s Next
As phishing attacks become more sophisticated, it’s crucial for iPhone users to stay informed and vigilant. Apple’s new guidelines provide essential steps to enhance online security. Users must remain cautious and proactive in protecting their personal information. By following Apple’s recommendations and staying aware of phishing tactics, users can significantly reduce their risk of falling victim to cyber threats.
Staying updated via Apple with the latest security measures. Further educating yourself on potential risks are key to maintaining secure online interactions in an increasingly digital world.
— Text-to-Speech (TTS) provided by gspeech